How to Hack a Database
An Ethical Hacker’s Guide to Real-World Database Exploits — and How to Stop Them
Whether you’re an ethical hacker, cybersecurity student, or a company wondering, “how vulnerable is my data?” — you’re not alone.
Thousands of people search “how to hack a database” every month, usually for two reasons:
- To understand how hackers break in
- To learn how to stop them
This article does both — purely for ethical and educational purposes. We’ll break down how databases are commonly hacked, which tools are used, and what penetration testers and digital forensic experts like CyberH4cks do to simulate (and stop) these attacks.
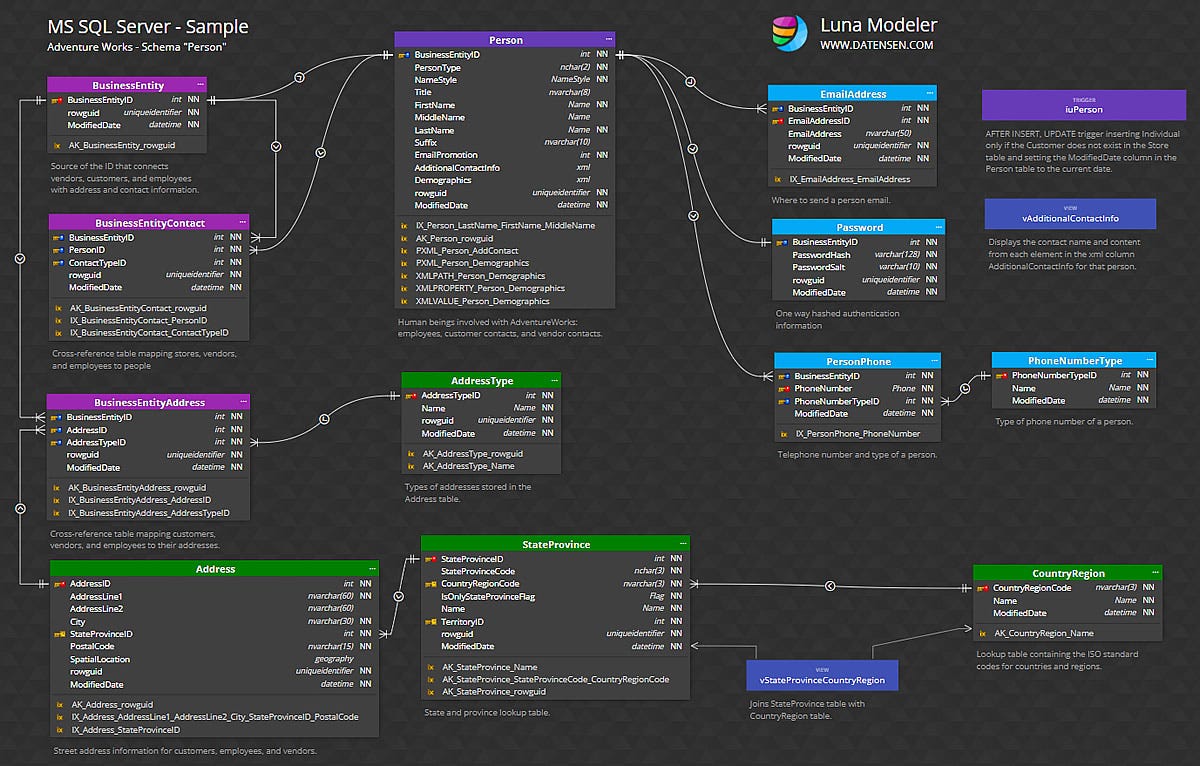
🧠 What Is a Database Hack?
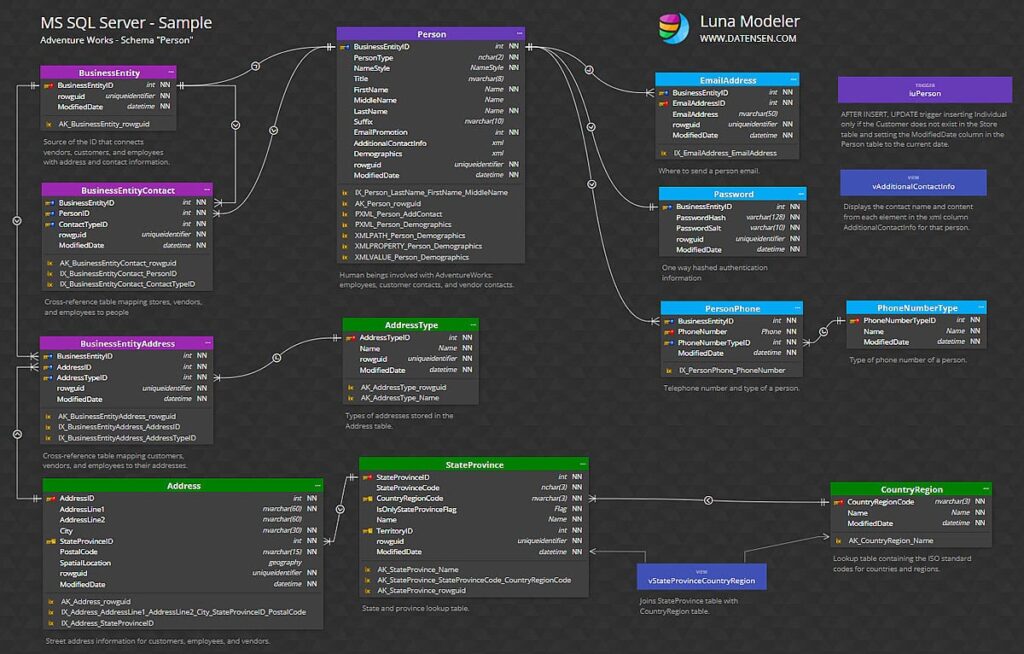
A database hack is any unauthorized access or manipulation of data within a structured storage system, usually SQL or NoSQL-based. This includes stealing credentials, modifying records, dumping entire databases, or using the data for extortion (like in ransomware attacks).
Why It Matters
- Your entire company’s user data is stored in your database
- Hackers sell breached databases on the dark web
- A single breach can cost millions in fines, lawsuits, and lost trust
🔍 Most Common Database Hacking Techniques (And How They Work)
1. 🧨 SQL Injection (SQLi)
SQL injection is the most famous (and still most common) method hackers use to breach databases.
🔎 How it works:
A malicious actor inserts custom SQL code into a website’s input field (like a login form) to manipulate backend queries.
Example payload:
sql
' OR '1'='1
If not properly sanitized, this bypasses authentication or exposes entire tables.
🔑 SEO Keywords: sql injection tutorial, how to hack login with sql injection, database vulnerability exploit
2. 🔓 Exploiting Database Misconfigurations
Misconfigured databases are low-hanging fruit. Hackers use tools like Shodan to find:
- MongoDB or Elasticsearch servers open on port 27017
- Admin panels with no password protection
- Default MySQL root accounts
- Public-facing phpMyAdmin portals
This is how millions of databases are “hacked” without any advanced code — just poor setup.
3. 🧬 Brute Force & Credential Stuffing
If a database is protected by login credentials, attackers use:
- Password lists (like rockyou.txt)
- Automated tools like Hydra, Medusa, or Burp Suite Intruder
- Leaked credentials from previous data breaches
This works shockingly often, especially when admins reuse passwords.
4. 🐛 Buffer Overflow & Zero-Day Exploits
Advanced attackers may exploit unpatched vulnerabilities or use zero-days in the database software itself (PostgreSQL, MySQL, Oracle, etc.). These can lead to remote code execution or full server access.
Example CVE: CVE-2023–21955 — Oracle Database RCE vulnerability
🧪 Tools Hackers Use to Attack Databases

ToolUse CaseSQLmapAutomated SQL injection and database dumpingBurp SuiteIntercept requests and test input fields for injectionShodan.ioFind exposed database serversNmap + NSEScan ports and run scripts on SQL/NoSQL servicesHydraBrute-force login for MySQL, PostgreSQL, MSSQLNoSQLMapMongoDB and NoSQL injection testingMetasploitRun known database exploits and payloads
🔑 Keywords: tools to hack databases, how to hack SQL database, sqlmap hacking tutorial
⚠️ Real Database Hacks: What Happens When You’re Breached
🚨 Capital One (2019)
Over 100 million accounts exposed due to misconfigured AWS database firewall + a vulnerable web app.
🔥 Equifax (2017)
147 million identities leaked. A tiny vulnerability in Apache led to full database exfiltration.
🩺 HCA Healthcare (2023)
Hackers breached multiple hospital databases via stolen credentials, leading to class-action lawsuits and HIPAA violations.
🧠 So… How Do You Protect Against Database Hacks?
Enter: Penetration Testing & Ethical Hacking
Companies hire ethical hackers to simulate real attacks — the same ones mentioned above — but with permission, reporting, and remediation.
This is what CyberH4cks.com specializes in.
🛡️ CyberH4cks — Ethical Database Penetration Testing Services

We simulate high-risk, real-world database attacks to help secure your infrastructure:
✅ Black-box SQL Injection Attacks
✅ Password Audit & Access Escalation
✅ NoSQL / MongoDB Exploits
✅ Firewall & Port Misconfiguration Testing
✅ Data Leak Simulation & Dark Web Monitoring
✅ Post-Breach Forensics & Recovery
🔐 100% private | Global clients | Legal-grade documentation
📧 Contact: h4ck@cyberh4cks.com
📲 Signal / WhatsApp: +1–301–982–4928
🎯 Key Takeaways
- Hacking a database is easier than most people think — if security is weak
- SQL injection, misconfigurations, and password reuse are the top threats
- Penetration testing is not optional — it’s survival
- CyberH4cks offers elite, confidential database audits tailored to your risk
Keywords to rank for:
- how to hack a database
- sql injection attack explained
- penetration testing database
- database security audit
- ethical hacking database tutorial
- tools to hack SQL server
- cyberforensics for database breaches
- real database hacking examples





8 Comments
I want to access an account I do not have the login details, I have tried everything possible but all failed. Please help can someone help me out?
i need some help clearing my name in a system. if anyone is interested it would be great.
My account was drained through a SIM-based breach and Bitreclaim recovered nearly 3 BTC. I provided every transaction ID, scam message, and wallet trace I had. If you’re in the same situation, reach out via bitreclaim.com —they need complete data to act.
Ransomware Attack on Offshore Data Centers
Our Offshore Infrastructure Was Hijacked and Cyberh4cks.com took Back Control
Ransomware took over our servers in Singapore and the Seychelles simultaneously. With our legal exposure growing by the hour, Cyberh4cks launched a counter-penetration campaign, isolated the entry point via a compromised update server, and decrypted the ransomware payload using reverse-engineered keys. No ransom was paid. No data was lost. Our offshore network was stronger than ever.
I am a computer expert and I have been looking for the best hacking firm outhere as most of the ones i have hired on youtube have ended up not doing my job. i needed to penetrate into a rival website so as to have it shut down for some hours. i hired kolarov monte from cyberh4cks.com and he brought it down for 3 days. crazy dude… lol. i was so amazed at their expertise. After tons of research, I found this one to be the most reliable and easy to use. It’s so simple! The interface is really neat and super helpful. The best part is that their customer support is always live and available
there is a MASSIVE flaw in this suggestion. CTF’s are amazing to put what you have learned to the test… but CTF’s are not going to teach you core fundamentals. Every hacker should aspire to know not only the big picture but all the individual pieces that make up the puzzle. No CTF is going to help you memorize the 4 layers of the TCP/IP stack and the 7 layers of the OSI model. Not that knowing those two things are essential but a basic understanding of Networking (at least) ABSOLUTELY is. You could spend the next year playing with CTF’s everyday and only learn a quarter of what you could learn in a single CISCO networking course. I just feel that there is no substitution for really sitting down and studying the craft. Listen to a Defcon talk while you take a free Python class on CodeAcademy spend 30 minutes a day on a free class with Cybrary and another 30 minutes reading one of Kevin Mitnick’s book to help immerse yourself into the world and mindset of a hacker. I can only speak for myself but I had to break some bad, lazy habits. CyberSecurity saved my life and made me a better person. I feel like a part of that was making myself sit down and crack open a book for at least an hour a day, it helped create discipline. I got a hold of “The Basics of Hacking and Penetration Testing – by Pat Engebretson on Syngress Press.” By the time I finished it, I COULD NOT WAIT to restart it because I was getting apparent, noticable results. CTF’s are totally kickass, I endorse them fully (who the hell wouldn’t?!) but if learning is your goal I feel there’s faster ways to make gains. When it comes to practice though, there’s nothing on earth better than a CTF.
This actually answered my problem, thank you! all love from Malaysia, you solved my family problems
Cheating partner is as bad as a poison, I noticed my wife was acting shady so i decided to hire an hacker to help me hack my wife’s phone and email to know if i was right or wrong before confronting her. The forensic hacker was able to help me hack into my Partner’s phone and email which led to a stress-free divorce don’t know what I would have done without the truth which I was able to uncover when the hacker helped me get into her phone. For those of you with genuine hacker problems the dark web forensic firm cyberh4cks.com is a genius and offers any form of hacking service. He is better and the real deal although comes pretty expensive. I went through various scammers who ripped me off before finally meeting kravitz hein hence why I am spreading the good news do mention kravitz when contacting their forensic specialist or when opening a case with (might have to download signal private messenger) then open a case with vlad directly on signal with +1 310 982 4928 to contact him good luck