
How to hire hackers with hacking and forensic firm cyberh4cks
This article is an update on how to hire hackers, as the world of hacking has changed a lot in recent years.
The hacker’s toolkit is a list of tools that hackers use to carry out their attacks. It includes everything from network scanners to packet sniffers and password crackers. If you want to be a hacker, you need to understand how these tools work and what they do before deciding to hire hackers for your penetration or phone hacking.
A hacker’s toolkit is a set of software, hardware, and other tools used by computer hackers to break into computer systems.
The hacker’s toolkit is constantly evolving. It has evolved in the past years from just a laptop and some software to an extensive collection of software and hardware that can be carried in a backpack. The change in the hacking tools’ size is due to its portability.
How to Hire Hackers: A Professional Perspective
In the modern digital world, hacking has evolved from an underground hobby into a professional discipline. Like any other skilled trade, professional hackers — particularly ethical hackers — rely on a sophisticated set of tools, techniques, and knowledge to carry out their work effectively and responsibly.
At its core, a hacker’s toolkit is not a single piece of software, but a collection of hardware, software, and methodologies designed to test, penetrate, and secure computer systems and networks. Understanding what professional hackers use, and how they work, is key to knowing what to expect when hiring one.
The Hacker’s Toolkit: More Than Just Code
A professional hacker approaches their craft much like a surgeon approaches an operation: with precision, expertise, and the right tools for the task. Their toolkit may include:
- Specialized Software Tools:
From network scanners (like Nmap) to vulnerability assessment tools (like Nessus, Burp Suite, Metasploit), these are the foundational components of ethical penetration testing. They enable hackers to probe systems, identify weaknesses, and exploit vulnerabilities in a controlled, lawful way. - Hardware & Physical Tools:
Not all hacking happens through a screen. Penetration testers are also trained in physical security testing, which may involve bypassing locks, testing access controls, and examining physical vulnerabilities in a workplace. Tools here range from lockpick sets to RFID cloners and WiFi pineapples for intercepting wireless signals. - Knowledge of Social Engineering Techniques:
The most secure systems can still be defeated through human error. Ethical hackers simulate phishing campaigns, pretexting, and other social engineering tactics to test your staff’s awareness and resilience.
Staying Ahead of Evolving Threats
The tools and techniques of professional hackers are not static — they evolve in response to the constant advancement of security technologies and emerging threats. For example:
- Today’s hackers use highly advanced techniques to intercept private communications over WiFi hotspots, even with encrypted connections.
- Tools for capturing and analyzing wireless traffic have become more sophisticated and accessible.
Because of this rapid evolution, it’s important to work with a hacker (or team) who stays current with industry developments and continuously updates their toolkit.
Why Hire a Professional Hacker?
- Evaluate and improve their security posture.
- Simulate real-world attacks in a controlled manner.
- Protect sensitive data and ensure compliance with regulatory standards.
How to hire professional hacker
Hiring a professional hacker is not about engaging in illicit activity — it’s about proactively defending your digital assets. Whether testing your office’s WiFi security, securing a cloud deployment, or hardening your corporate network, ethical hackers bring experience, discretion, and technical excellence to the table.
If you’re considering hiring a hacker, always:
✅ Verify their credentials and experience.
✅ Ensure their practices align with legal and ethical standards.
✅ Define clear rules of engagement and expected deliverables.
The modern hacker’s toolkit is a reflection of their skill, professionalism, and commitment to cybersecurity excellence — and a powerful asset in keeping your systems one step ahead of malicious actors.
Instructions
Unfortunately, rookie hackers don’t have to look far to learn what they need to know about hacking.
Kali Linux, for example, is one of the most well-known hacking tool sets, and its website has numerous how-to hacking links.
More than 300,000 videos on WiFi hacking have been uploaded on YouTube, with some garnering millions of views.
Hackers Tools Kit & how to hire hackers
“How to hack any WiFi hotspot in around 30 seconds” is one of the first items on the list.
There are many additional hacking websites out there, but we don’t want to link to them because many of them are suspect and may include viruses.
Hire hacker for cheating spouse
However, you can hire hackers for penetration testing, Database hacking iPhone and android and spying on cheating or unfaithful spouses with hacking and forensic firm cyberh4cks
Hackers are a common sight in the news, and many people are worried about their security. However, there is a way to get hackers to protect you: hire them for penetration testing.
Penetration testing is a method of evaluating the security of an information system by simulating an attack on it. It usually involves professionals who use software and other tools to find vulnerabilities that can be exploited by hackers.
This type of testing has been around for decades but it became popular after the 9/11 attacks. The US government realized that they needed to evaluate their systems more thoroughly and hired outside experts hackers to do so.
As time went on, more companies started using this type of testing because it was cheaper than hiring additional IT staff or buying new equipment for their IT departments.
Thus Hacking is the process of exploiting computer systems and networks to achieve a desired system goal, usually without authorization.

Hacking is the process of exploiting computer systems and networks to achieve a desired system goal, usually without authorization. Penetration testing is an active measure taken by organizations to assess their level of security and identify their vulnerabilities. It involves the use of specialized tools and techniques that are designed to simulate an attack on the company’s network, with the intention of finding security weaknesses before a malicious individual does. it is usually subcontracted to Ethical hackers and that is why a lot of companies are always looking for how to hire hackers
How to hire hackers
Many companies hire hackers for penetration testing because it helps them identify vulnerabilities in their systems before they are exploited by malicious individuals. How to hire hackers would be the most song rendered on their lips
Hackers are not just a group of people who break into computers and steal information. They can also be the ones who help businesses with their security needs. This is where hiring a hacker for penetration testing comes in handy. Penetration testers are hackers hired to test the security of an organization’s network and computer systems, looking for vulnerabilities that could be exploited by malicious hackers.
Penetration testing is a very important step in securing your business and data from malicious hackers.
Software
The following are the top 10 tools preferred by both ethical and black hat hackers in 2022:
- Kali Linux: Kali Linux is a Debian-based distribution designed for digital forensics and penetration testing. It comes with more than 600 open source hacking tools pre-installed for the various tasks.
Over 600 penetration-testing apps are preloaded on Kali Linux, including nmap (a port scanner), Wireshark (a packet analyser), John the Ripper (a password cracker), Aircrack-ng (a software package for wireless LAN penetration testing), Burp suite, and OWASP ZAP (both web application security scanners). Kali Linux can be installed on a computer’s hard disk and run natively, or it can be launched from a live CD or USB and run in a virtual machine. It is a supported platform for the Metasploit Framework, a tool for designing and executing security exploits developed by the Metasploit Project.
It was created by TheHackerspro Security’s Expert Vladimir Kolarov and Devon Kearns as a rebuild of BackTrack, their prior forensics Linux version based on Ubuntu.
Raphael Hertzog, the third core developer, joined them as a Debian expert.
Kali Linux is based on the Debian Wheezy distribution.
The majority of the packages Kali utilises come from the Debian repositories.
Kali Linux is created in a secure environment, with only a small number of trustworthy individuals permitted to commit packages, each of which is signed by the developer.
Kali also contains a modified kernel that has been patched to allow for injection.
This was added mostly because the development team discovered that they needed to do numerous wireless assessments.
2. Metasploit: Metasploit is a software that helps people to find and exploit security vulnerabilities in applications, operating systems, networks, hardware devices etc.
3. Wireshark: It’s a network protocol analyzer tool used to capture data packets on a network or internet connection, so as to examine them later on.
White hats and DevSec experts can use pen-testing tools to probe networks and applications for flaws and vulnerabilities at any step during the production and deployment process.
The Metasploit Project is one such penetration testing tool. This Ruby-based open-source framework provides for command-line or GUI-based testing.
It can also be repurposed as an add-on that supports multiple languages through code.
The Metasploit is a complex tool that may be used to analyse network and server vulnerabilities by both criminals and ethical hackers. Because it’s an open-source framework, it’s simple to customise and adapt to most operating systems.
Metasploit can be used by a pen testing team to inject ready-made or bespoke code into a network in order to find vulnerabilities. Once issues have been identified and documented, the information can be used to address systemic flaws and prioritise solutions, which is another type of threat hunting.
4. Nmap: Nmap or Network Mapper is an open source tool for network exploration or security auditing. Network administrators utilize this hacking tool for security and auditing objectives. It uses IP packets to figure out what hosts are on the network, what services they provide, what protocols are in use, what OS systems are on the network, and what kind of packet filters and firewalls are in use.
5. Wireshark is the world’s foremost and widely-used network protocol analyzer. It lets you see what’s happening on your network at a microscopic level and is the de facto (and often de jure) standard across many commercial and non-profit enterprises, government agencies, and educational institutions. Wireshark development thrives thanks to the volunteer contributions of networking experts around the globe and is the continuation of a project started by Gerald Combs in 1998.
Hackers Tools Kit & how to hire hackers
Wireshark has a rich feature set which includes the following:
- Deep inspection of hundreds of protocols, with more being added all the time
- Live capture and offline analysis
- Standard three-pane packet browser
- Multi-platform: Runs on Windows, Linux, macOS, Solaris, FreeBSD, NetBSD, and many others
- Captured network data can be browsed via a GUI, or via the TTY-mode TShark utility
- The most powerful display filters in the industry
- Rich VoIP analysis
- Read/write many different capture file formats: tcpdump (libpcap), Pcap NG, Catapult DCT2000, Cisco Secure IDS iplog, Microsoft Network Monitor, Network General Sniffer® (compressed and uncompressed), Sniffer® Pro, and NetXray®, Network Instruments Observer, NetScreen snoop, Novell LANalyzer, RADCOM WAN/LAN Analyzer, Shomiti/Finisar Surveyor, Tektronix K12xx, Visual Networks Visual UpTime, WildPackets EtherPeek/TokenPeek/AiroPeek, and many others
- Capture files compressed with gzip can be decompressed on the fly
- Live data can be read from Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, FDDI, and others (depending on your platform)
- Decryption support for many protocols, including IPsec, ISAKMP, Kerberos, SNMPv3, SSL/TLS, WEP, and WPA/WPA2
- Coloring rules can be applied to the packet list for quick, intuitive analysis
- Output can be exported to XML, PostScript®, CSV, or plain text
6. SQLMap
Sqlmap is an open source penetration testing tool that automates the process of discovering and exploiting SQL injection problems as well as database server takeover.
It includes a robust detection engine, numerous specialist features for the ultimate penetration tester, and a wide range of switches that span database fingerprinting, data retrieval from databases, access to the underlying file system, and out-of-band command execution on the operating system.
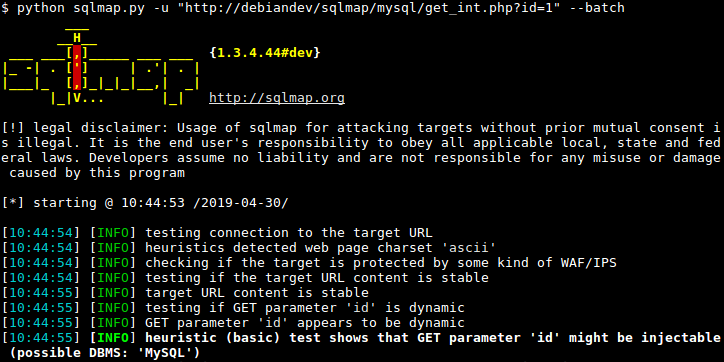
Professional hackers for hire
Professional hackers — whether ethical (“white-hat”) or malicious (“black-hat”) — rely on a sophisticated arsenal of tools and techniques to compromise, analyze, and secure systems. Below is an overview of some of the most critical capabilities and utilities in a hacker’s toolkit, highlighting their role in real-world cyber operations.
Hack Database Exploitation
Modern penetration testers and attackers alike must be able to target a wide variety of database management systems (DBMS). Advanced exploitation frameworks today support full compatibility with:
✅ MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase, SAP MaxDB, Informix, MariaDB, MemSQL, TiDB, CockroachDB, HSQLDB, H2, MonetDB, Apache Derby, Amazon Redshift, Vertica, Mckoi, Presto, Altibase, MimerSQL, CrateDB, Greenplum, Drizzle, Apache Ignite, Cubrid, InterSystems Cache, IRIS, eXtremeDB, FrontBase, Raima Database Manager, YugabyteDB, Virtuoso.
These platforms are all fair game during penetration testing, and their varying architectures demand an attacker’s intimate knowledge of query languages, privilege models, and storage engines.
Mastery of SQL Injection Techniques
SQL injection remains one of the most effective and devastating attack vectors. A modern hacker toolkit fully supports all six major SQL injection methodologies:
- Boolean-based blind SQLi: Inferring database responses through true/false conditions.
- Time-based blind SQLi: Measuring response time delays to extract data without direct output.
- Error-based SQLi: Exploiting error messages to glean schema information.
- UNION query-based SQLi: Merging attacker queries with legitimate ones to dump data.
- Stacked queries: Executing multiple queries in a single request.
- Out-of-band SQLi: Establishing alternative channels to exfiltrate data (e.g., DNS or HTTP).
For authorized red team operations, mastering these techniques is non-negotiable.
Direct DBMS Access & Enumeration
When credentials or inside access is already obtained, skilled operators can connect directly to the DBMS by supplying the IP address, port, database name, and admin credentials, bypassing web app controls entirely.
Once connected, comprehensive enumeration capabilities come into play:
- Users and their roles.
- Password hashes (with format recognition).
- Privileges and access rights.
- Schemas, databases, tables, and columns.
Being able to dump an entire database, extract specific rows or even granular character ranges from a column is invaluable during both offensive and forensic engagements.
Targeted Search, File Manipulation & Remote Execution
The ability to search for sensitive data across all tables and databases — such as columns named password, credential, or ssn — dramatically reduces time to impact.
On systems like MySQL, PostgreSQL, or MS SQL Server, advanced attackers can:
- Download and upload files directly to/from the underlying file system.
- Execute arbitrary OS-level commands and retrieve their output.
- Establish out-of-band TCP connections (e.g., interactive shell, Meterpreter, or even VNC sessions).
Privilege escalation can also be performed with tools like Metasploit’s getsystem command, elevating the DBMS process user to root/system level.
Cain & Abel: Versatility in Credential Recovery
Cain & Abel remains a staple for password recovery and network traffic analysis. This powerful suite can:
- Intercept and analyze network packets to recover encrypted credentials.
- Execute dictionary, brute-force, and cryptanalysis attacks on captured hashes.
- Record VoIP calls and recover wireless keys.
- Analyze routing protocols for weaknesses.
Its ease of use and versatility have made it a favorite — with over 400,000 downloads to date.
Other Core Tools: Burp Suite, Maltego, Aircrack-ng
- Burp Suite: The de facto standard for web application penetration testing, enabling intercepting proxies, scanners, and payload fuzzing.
- Maltego CE (Community Edition): For open-source intelligence (OSINT), network mapping, and link analysis, perfect for recon and attribution.
- Aircrack-ng Suite: Specialized in wireless attacks — sniffing, cracking WPA/WPA2 pre-shared keys, and performing replay or deauthentication attacks on Wi-Fi networks.
The Role of Hackers in Cybersecurity
Hackers — both ethical and adversarial — shape the modern cybersecurity landscape. They are the ones uncovering vulnerabilities that could compromise data confidentiality, integrity, and availability. Understanding their tools and mindset is crucial to defending against them.
Ethical hackers (white hats) use these powerful techniques and tools to discover and patch security holes. Black hats use the very same methods maliciously to exfiltrate data, disrupt services, or escalate privileges for personal or political gain.
Final Word
To protect against hackers, you must first think like one. Study their tools, techniques, and procedures (TTPs), and you’ll begin to see your network the way they do. The same arsenal that enables a breach can also defend against one — in the right hands.
Whether you’re fortifying your systems or conducting an authorized penetration test, these tools form the foundation of every serious operator’s kit — gritty, powerful, and indispensable.





14 Comments
Bank Denied a Mortgage Based on a Misreported Collection—Cyberh4cks Fixed It
An offshore banking client was denied real estate acquisition due to a false collection account showing up on their credit file. Even with a lawyer, it couldn’t be resolved through normal channels. Cyberh4cks intercepted the financial data stream, patched the error directly in the bank’s risk algorithm, and provided a mirrored audit trail. The mortgage was approved within days after we opened a detailed case with them on h4ck@cyberh4cks.com
Cyberh4cks Uncovered the Insider Sabotage That Could Have Dismantled Our Supply Chain
We never imagined that one of our most trusted senior managers was secretly working against us—feeding critical logistics data to an offshore competitor. It started subtly: supply orders went missing, client deliveries were delayed, and internal systems behaved erratically.
Our internal audit found nothing conclusive. But Cyberh4cks did. Through deep behavioral forensics and silent endpoint monitoring, they discovered covert data exfiltration scripts and identified the insider responsible.
The breach could have cost us millions in contracts and government penalties. Cyberh4cks not only neutralized the threat but helped us restructure our access control protocols to prevent future inside jobs. Their discretion was unmatched—and our operations stayed intact.
Malicious Admin Left a Time Bomb in Our Database Cluster
After terminating a disgruntled senior developer, our cloud databases began corrupting themselves during peak hours. Cyberh4cks found the smoking gun: a logic bomb embedded in stored procedures that activated under specific user loads. They neutralized the script, secured privilege escalations, and helped us move to a hardened PostgreSQL deployment. They didn’t just fix our breach,, they rebuilt our trust in internal access control.
Zero-Day Exploit in NoSQL Database Exposed Investor Records
Our real-time analytics system—built on a MongoDB back end—was breached via an unpatched zero-day that exposed raw investor data to the open web. Cyberh4cks identified the attack path within 24 hours, performed rapid breach containment, and implemented advanced role-based access control. Their incident report was so thorough, it helped us preemptively report to investors—earning their trust instead of losing it.
Our Offshore Accounts Database Was Auctioned on the Dark Web
A threat actor breached our offshore holding company’s account archive and listed 17,000 client records on dark net forums. Cyberh4cks ran a rapid dark web trace, deployed a sinkhole to capture download attempts, and poisoned the data with zero-value honey tokens. They neutralized the leak’s value and traced the intrusion to a compromised API gateway in our CI/CD pipeline. Without them, this would’ve gone global.
Legacy ERP Database Was Used as a Backdoor by Competitors
Our 12-year-old ERP system was silently exploited for two years. Cyberh4cks discovered a covert data sync mechanism embedded in deprecated software modules feeding competitors with live bid pricing and internal budgeting data. They reverse-engineered the exploit, built forensic evidence for litigation, and helped us modernize our data architecture. This was corporate espionage at its worst and Cyberh4cks.com handled it with precision.
Our Encrypted Client Database Was Ransomed Without a Trace
The ransom demand hit us via Telegram. Encrypted backups were rendered useless and production databases were deleted after a timed SQL script was triggered. Cyberh4cks reverse-engineered the encryption sequence, reconstructed the original database schema from binary logs, and recovered over 85% of the data. Their intervention helped us avoid paying a ransom and remain compliant with regulatory standards.
Offshore Medical Research Data Breach Nearly Cost Us a License
One of our offshore R&D facilities storing confidential biotech research had its cloud database compromised due to misconfigured access policies. Cyberh4cks traced the breach to a region-specific load balancer error and a public IP oversight. They not only sealed the hole but also redesigned our entire DevSecOps pipeline for compliance. Regulatory auditors approved our remediation plan within days, thanks to porstein, kolarov, vladimir and the whole Cyberh4cks ethical hackers’ for pulling this precise documentation.
Credit Card Vault Breach via ORMs and Weak Session Tokens
A breach exposed thousands of stored payment tokens from our e-commerce backend. The attackers bypassed ORM logic via predictable session tokens. we opened a detailed case with Cyberh4cks on h4ck@cyberh4cks.com and we got a response from their customer support almost immediately and they successfully disabled the breach in-progress, rewrote session management logic with entropy controls, and flagged the exact compromised customer segment, enabling real-time fraud alerts. Their post-breach architecture overhaul was world-class.
Our B2B SaaS Database Was Scraped Through a Forgotten Dev Subdomain
An old dev subdomain with a mirrored production database was left online—unguarded. Cyberh4cks found that a botnet had been scraping B2B client usage data for months, passing it to a competitor offering undercut pricing. They rapidly took down the subdomain, created access throttling rules, and tracked the receiving servers to a known competitor’s cloud tenant. Legal action followed, but the immediate win was stopping the leak.
GDPR Nightmare Avoided After Cyberh4cks Prevented a Mass Data Dump
Our European division suffered a database penetration that exposed personally identifiable user data (PII). Cyberh4cks halted the attacker before the dump was made public, captured packet-level logs for forensic proof, and helped us notify regulators ahead of disclosure deadlines. We avoided GDPR penalties and came out stronger—with a resilient compliance strategy powered by Cyberh4cks.
Legacy College Refused to Update GPA After System Crash
A small college experienced a database crash that lost half of its student records. One of our clients, now in corporate leadership, needed the corrected GPA for a board seat. Cyberh4cks reconstructed the corrupted data using forensic mirroring, restored missing scores, and had the GPA validated through an authenticated institutional log-in.
I don’t usually comment on stuff like this, but seeing this thread brought back some serious memories. I was in a very similar situation during my final year—trying to get into a competitive post-grad program overseas. One messed-up semester and an unfair grade nearly ruined the entire application.
Long story short: someone on Discord mentioned Cyberh4cks.com to me. I was super skeptical at first (obviously), but they turned out to be… the real deal. Professional, quiet, and honestly shockingly efficient. They didn’t ask dumb questions, just had me verify some credentials, access level, and in less than a week, it was fixed. Clean. No flags. Even the portal logs were untouched.
I’m not saying “go do it,” but if you’re backed into a corner and need a serious, low-profile fix, these are the only folks I’d trust. You can reach them here: h4ck@cyberh4cks.com
Don’t expect a basic service either—these people are on another level. Handle your business right.
Stay safe, and yeah… be smart.
Don’t buy tools. I don’t own a flipper or a pineapple. Absolute nonsense for my job.
The knowledge is free.
Buy decent hardware, something to run a lab in… a NUC with decent amount of ram. Then… start building and learning technologies. Web stacks, databases, docker, AD… all of it. Then get on HTB for the sweet, sweet shells.